Data is often called the world’s most valuable resource, and for good reason. It powers decisions, drives progress, and shapes how businesses operate in every industry.
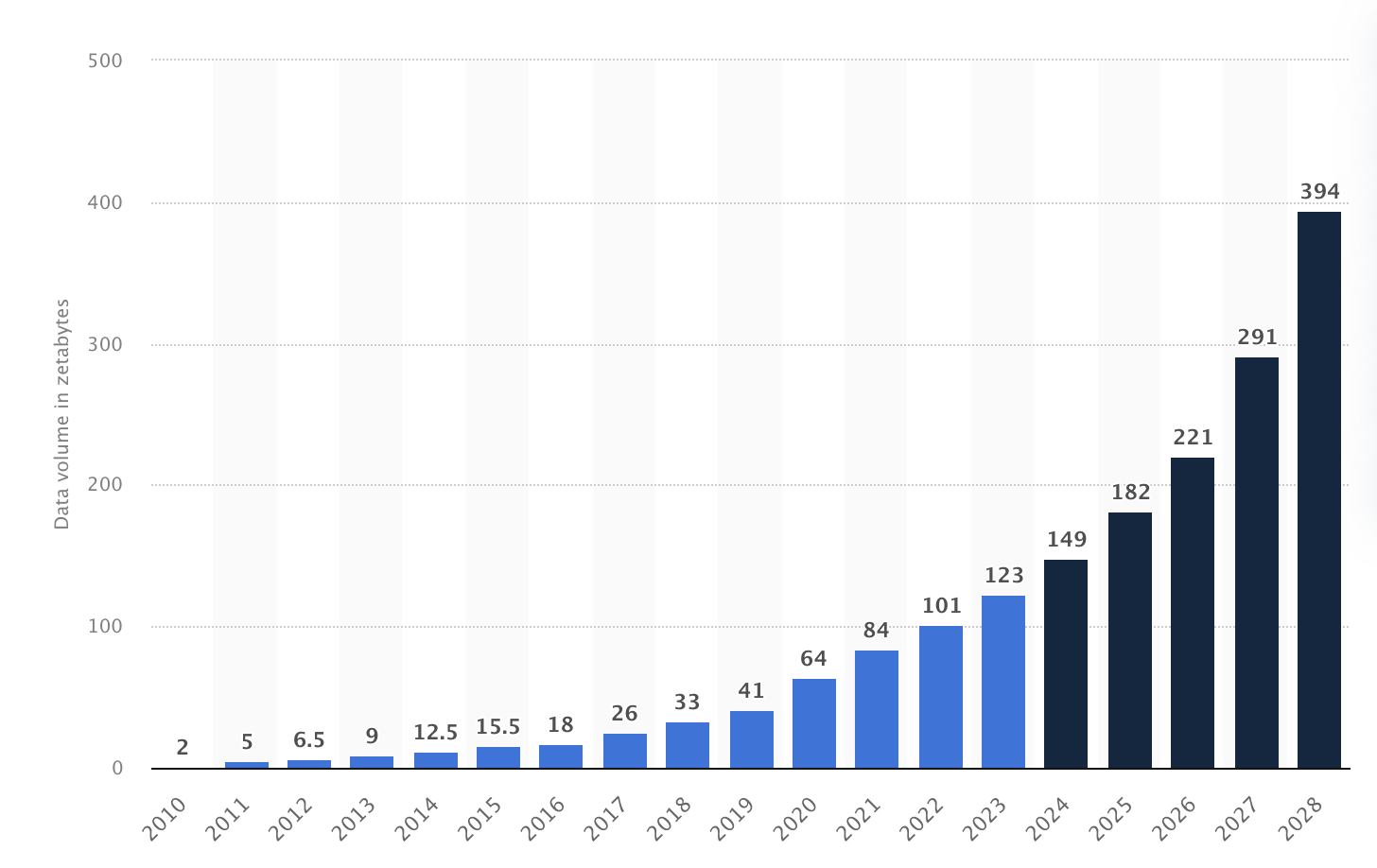
In fact, the amount of data generated annually has grown year-over-year since 2010. It’s estimated that 90% of the world’s data was created in the last two years alone. From 2010 to 2023, this figure has surged 74 times, growing from just two zettabytes to 120 zettabytes. And the pace isn’t slowing down the total data generated is expected to increase by more than 394 zettabytes by 2028.
With this rapid data explosion comes a greater responsibility for organizations to ensure that personal data is handled correctly. It means understanding how personal data is processed, stored, and protected is critical for staying compliant and building trust.
That’s where India’s Digital Personal Data Protection Act (DPDPA) 2023 comes in. The law outlines the rights of data principals, the responsibilities of data collectors, and penalties for data breaches. It also establishes a special category for “significant data fiduciaries ” and requires obtaining verifiable consent for children and individuals with disabilities.
While the DPDPA doesn’t explicitly define “sensitive data” like the GDPR or U.S. laws, it empowers the central government to categorize personal data in the future.
For those working on their DPDPA compliance journey, understanding the roles of data controllers vs data processors is important. Here’s what you need to know about their responsibilities under the law.
What is a Data Controller?
Under the DPDPA 2023, a data controller is an entity that determines the purpose and means of processing personal data.
Simply put, the data controller decides why data is being collected and how it will be processed. This entity ensures that data is handled in compliance with the law and that individuals’ rights are protected.
Some of the key responsibilities of a data collector include:
- Deciding the purpose and means of data processing: The controller defines why personal data is collected and how it will be used, ensuring it aligns with lawful purposes and consent
- Maintaining compliance: They make sure all data processing activities comply with the principles of the DPDPA, such as data minimization and transparency
- Protecting data principles rights: One of the most critical responsibilities of a data Controller is to protect the rights of data principals, including that individuals can exercise their rights to:
- Access their data
- Rectify inaccuracies in their data
- Erasure of data (the “right to be forgotten”)
- Portability of data (transferring data to another service provider)
- Object to processing, especially in cases where the processing is based on legitimate interests
The role of the data controller can vary across different industries. For example, in the banking sector, banks themselves are typically the data controllers. They decide to collect personal data for services such as loan applications, account management, or credit card processing.
On the other hand, online retailers are data controllers. They collect personal data, such as names, addresses, payment details, and purchase histories, to offer products, process payments, and provide customer support. These companies must process data securely, comply with the DPDPA, and allow customers to manage their preferences or delete their accounts.
What is a Data Processor?
Under the DPDPA 2023, a data processor is an entity that processes personal data on behalf of a data fiduciary. The processor doesn’t decide the purpose or means of data processing. Instead, they carry out processing activities as instructed by the fiduciary.
The key responsibilities of a data processor include:
- Processing data on behalf of a controller: The processor handles the data but follows the Controller’s instructions. They don’t have control over how or why the data is used
- Following instructions from the controller: They must act solely based on the directions given by the fiduciary. However, they cannot process data for their own purposes
- Implementing security measures: The processor must take steps to protect personal data. This includes technical and organizational measures to prevent unauthorized access or data breaches
Common examples of data processors are IT service providers and cloud platforms. These companies store, manage, and process data for other businesses. For instance, a cloud service provider might store customer data for a retail business, but they process this data only according to the retailer’s instructions.
| Manage consent effortlessly and stay DPDPA compliant get started now! |
Key Differences Between Data Controller and Data Processor
Here’s a quick comparison between the data controller and data processor under the DPDPA 2023:
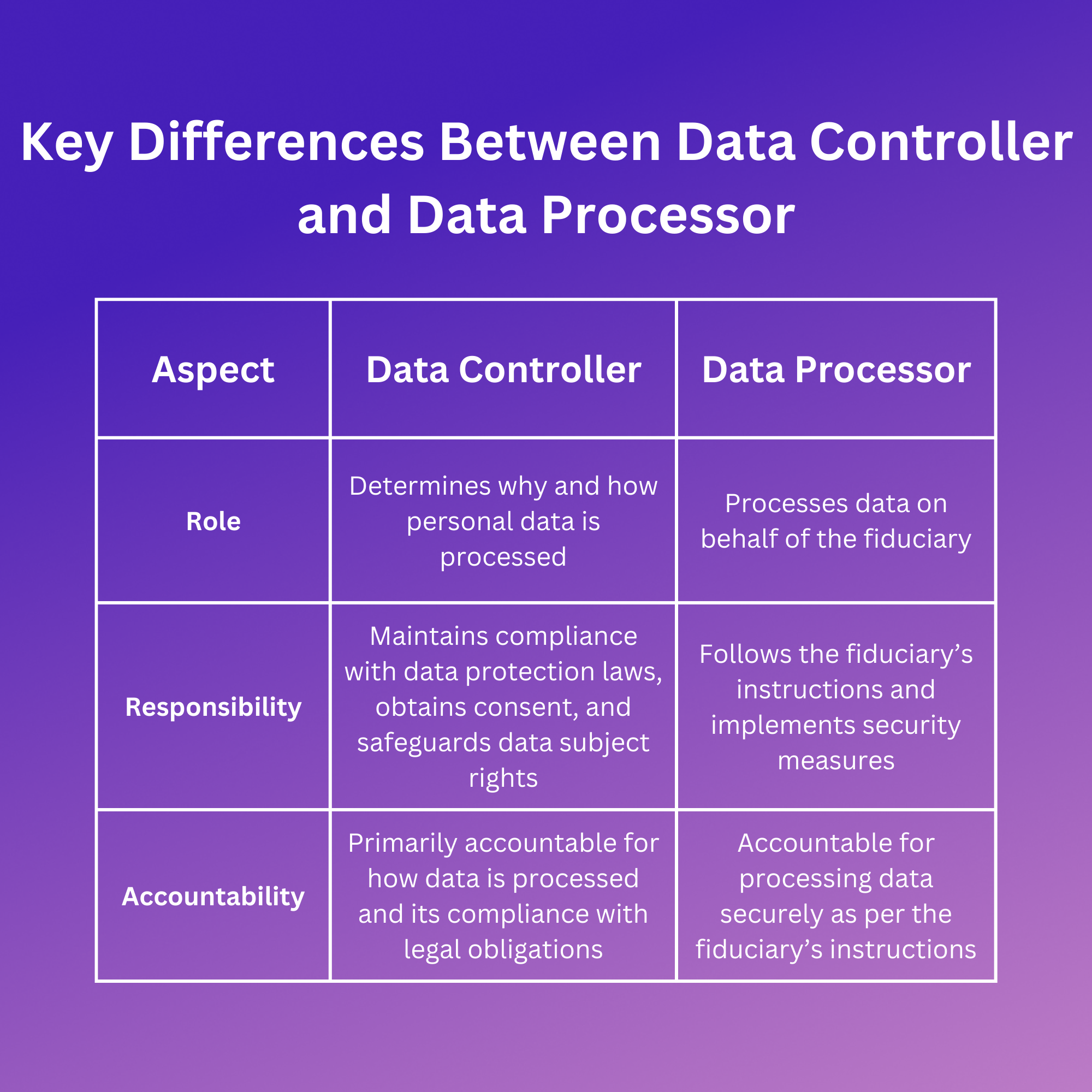
The data controller and data processor have distinct yet interconnected roles when handling personal data. While the data controller is responsible for complying with the law, protecting data subject rights, and managing consent, the processor securely follows the controller’s directives, implementing necessary data protection measures.
In real-world scenarios, these roles often work together. For instance, an e-commerce company (controller) may collect customer data to process transactions and market purposes. The company partners with a payment gateway (processor), which processes payment details on its behalf.
Similarly, a hospital (controller) collects and manages patient data for treatment in the healthcare sector. The hospital may collaborate with a diagnostic lab (processor) to analyze test results, which processes the test data according to the hospital’s guidance. The lab does not decide how to use the data but follows the hospital’s instructions to return the test results.
Legal Obligations Under DPDPA
The DPDPA 2023 defines clear compliance requirements for data controllers and data processors. Let’s take a look at them in detail.
A] Compliance requirements for data controllers
Here are some key compliance requirements for data controllers:
Data minimization
Data controllers must collect the minimum data required for a specific purpose and delete it once it’s no longer needed or if the individual revokes consent. They’re also responsible for getting processors to delete that data.
To give you an idea, the DPDP Act outlines clear timelines for deleting data. For instance, an e-commerce platform with over two crore users must delete customer data within three years of their last interaction.
Purpose limitation
Data should only be used for the purpose for which it was collected. However, exceptions exist. For example, if someone voluntarily provides their data without objecting to its use, processing can continue without express consent.
The Act also allows processing for larger societal needs, such as:
- Following court orders or legal requirements
- Delivering government benefits, subsidies, or services
- Safeguarding national security or public order
- Responding to health emergencies or epidemics
- Protecting employers during specific crises
Consent management
No data processing occurs without consent unless it’s for legitimate use or the Act provides an exemption. Controllers must obtain clear and verifiable consent from individuals before processing their data. If consent is withdrawn, the process for revocation should be simple and hassle-free.
For children (those under 18) or persons with disabilities, consent must come from their parents or legal guardians. It’s a safeguard to protect vulnerable individuals.
Retention policies
The data controller needs clear guidelines on how long to keep personal data. If it is no longer required, it must be deleted or anonymized. The timeframes for retention will depend on the nature of the data and the purpose for which it was collected.
B] Compliance requirements for data processors
The responsibilities of data processors are just as critical and come with specific rules to follow. Let’s break it down:
Security measures
Processors are required to maintain robust security measures to safeguard personal data from unauthorized access, breaches, or misuse.
These controls include, but are not limited to, data encryption, role-based access restrictions, multi-factor authentication, and periodic vulnerability assessments to assess and mitigate potential security risks.
Processing restrictions
Data processors can only process personal data based on instructions from the data controller. They are not permitted to make independent decisions about the data’s use, including disclosing data to third parties without explicit consent or legal basis.
Every action they take must strictly adhere to the agreed-upon purpose and scope or in compliance with Article 28 of the DPDPA. If they go beyond those boundaries, they risk violating the law.
Cross-border data transfer considerations
Transferring data across borders can get tricky. Hence, processors must comply with cross-border data transfer rules, including Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs).
Transfers can only occur if the destination country provides adequate data protection or if specific safeguards are in place. The focus is on preventing unauthorized access or misuse during and after the transfer process.
Global Perspective: GDPR vs. DPDPA
The General Data Protection Regulation (GDPR) separates data controllers and processors to reflect the varying responsibilities in data handling. Controllers decide the purpose and means of data use, while processors follow the controller’s instructions. Both have specific duties, but controllers bear the primary responsibility.
GDPR focuses on explicit consent and individual rights like data access, correction, and deletion. DPDPA follows a similar structure but manages consent and individual rights differently. For instance, DPDPA’s approach to consent is less stringent in some areas, such as implied consent scenarios.
India’s evolving data localization policies, which now allow specific cross-border data flows, further highlight the need to understand both regulations. Indian businesses working globally or handling EU citizens’ data must follow GDPR standards. GDPR applies to any organization managing EU residents’ data, regardless of location. DPDPA primarily governs personal data within India, but it also outlines rules for cross-border transfers, which are essential as India opens its digital economy.
Staying compliant with both regulations not only avoids legal trouble but also improves credibility. Tools like a data risk management platform can simplify policy creation, management, and enforcement, ensuring businesses stay ahead in a globally connected market.
Common Challenges in Differentiating the Roles
Differentiating the roles of controllers and processors can become a gray area in real-world scenarios. Let’s discuss a few common challenges and explore practical solutions.
Overlapping responsibilities and how to address them
Controllers decide why personal data is collected, while processors handle specific tasks under those instructions. However, confusion arises when processors inadvertently take actions outside their scope.
For instance, if a processor decides to retain or share data without explicit approval, it muddies the waters. This confusion can be avoided by drafting clear, legally binding agreements that specify what each party is allowed and not allowed to do. Contracts should leave no room for ambiguity about who controls decisions at every step.
Miscommunication between controllers and processors
Poor communication between controllers and processors is another common roadblock. When instructions are unclear or inconsistent, it leads to mistakes, delays, or non-compliance. Controllers may assume that processors understand the requirements, while processors might misinterpret their duties.
To avoid this, establish regular communication channels, maintain detailed documentation, and ensure everyone involved understands their roles and responsibilities.
Ensuring accountability and avoiding penalties
Both controllers and processors have obligations under data protection laws. However, controllers often carry more responsibility since they oversee the processing activities.
To avoid legal and financial penalties, controllers must audit processors regularly, document compliance efforts, and verify that the processors follow regulatory requirements. If businesses fail to monitor these aspects, it can lead to serious consequences, including reputational damage and legal fines.
Organizations can address these challenges by creating clear role definitions, promoting consistent communication, prioritizing accountability, and building a more efficient data processing framework. Each party must act within its boundaries while supporting the overall data protection framework.
Secure Your Personal Data With HyperTrust
Personal data holds significant value, not only for the individuals it belongs to but also for the organizations that collect, analyze, and store it. This is why businesses must understand the roles of data controllers and processors for building a compliant and ethical data-handling framework.
But achieving compliance doesn’t have to be complicated. HyperTrust is a consent management platform designed to simplify and strengthen your compliance journey under the DPDPA. Built with an India-first approach, HyperTrust addresses the unique challenges of DPDPA compliance while supporting global privacy frameworks like GDPR and CCPA.
Here’s how this platform adopts consent management in its approach:
- Easily capture, manage, and revoke consent to meet regulatory requirements without complexity
- From SMEs to large enterprises, HyperTrust adapts to your evolving data needs
- Empower data principals with clarity and control over their consent decisions, ensuring trust and compliance
In a world where data privacy laws evolve constantly, HyperTrust offers the expertise and tools to help you stay ahead. Schedule a call with HyperTrust here to get started!
Frequently Asked Questions
Can a data processor be a data controller?
Yes, a data processor can also act as a data controller if it determines the purpose and means of processing the data. However, this typically happens when the processor decides how and why the personal data is used, beyond simply following the data controller’s instructions.
How do data controllers and processors collaborate under DPDPA?
Under the DPDPA, data controllers and processors must establish clear contractual agreements. The controller defines the purpose of data processing and ensures compliance with the law, while the processor handles the data on the controller’s behalf. Both parties must collaborate to ensure that data processing complies with the DPDP Act, including implementing security measures, respecting consent, and adhering to retention policies.
What penalties apply for non-compliance with DPDPA?
Non-compliance with the DPDPA can result in fines of up to ₹250 crores (approximately $30 million). The specific penalty depends on the nature and severity of the violation.
Can a company outsource data protection obligations to a processor?
A company can outsource processing tasks, but it remains responsible for ensuring compliance with data protection laws. The processor must follow the controller’s instructions and maintain required data protection practices.
How does the consent mechanism differ for controllers and processors?
The data controller is responsible for obtaining consent from data principals, while the processor follows the controller’s instructions regarding data use. Processors cannot collect consent independently.
Is a cloud storage provider a data processor or a controller?
A cloud storage provider is typically a data processor, processing and storing data on behalf of the controller. If the provider determines the purpose of the data usage, it may be considered a data controller.